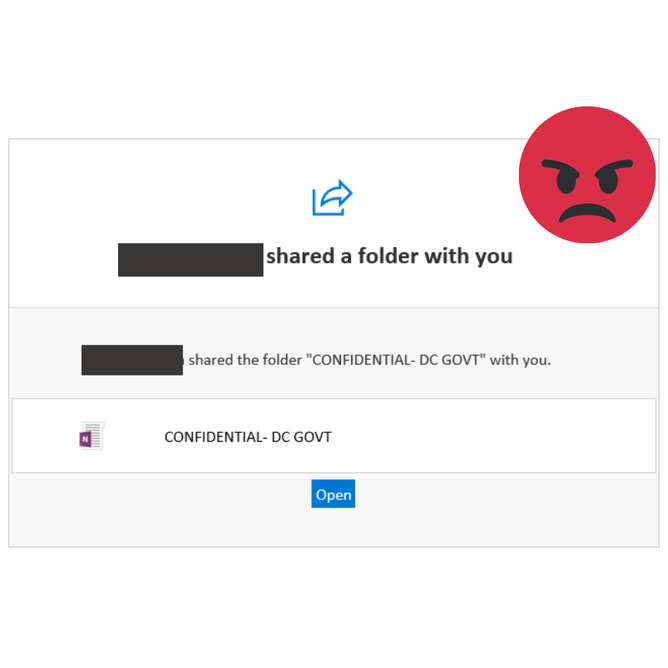
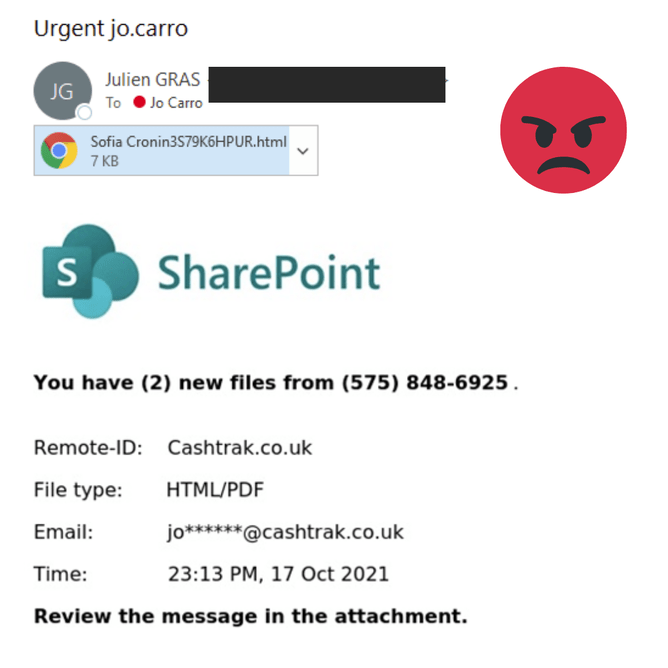
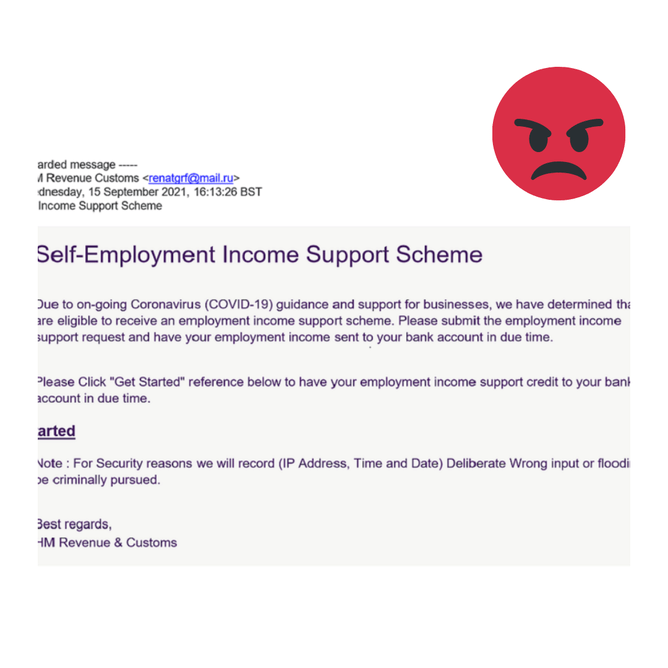
Cyber scams are on the increase again, we have been targeted twice in as many weeks with suspicious e mails and wanted to draw attention to these e mails. We want to raise awareness that these seemingly genuine looking e mails are should not be opened, they are phishing* e mails and should be deleted.
*Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message.
The National Cyber Security Centre (NCSC) provide the following guidance on protecting businesses and charities.
Spotting suspicious messages
Spotting scam messages and phone calls is becoming more difficult with many scams even fooling experts. There are some tricks that criminals will use to try and get you to respond without thinking. Things to look out for are:
- Authority - the message claiming to be from someone official. For example, HMRC, your bank, doctor. Criminals often pretend to be important people or organisations to trick you into doing what they want.
- Urgency - you have a limited time to respond. Criminals often threaten with fines or other negative consequences.
- Emotion - the message makes you panic, fearful or curious. Threatening language is often used making false claims of support or to tease you into wanting to find out more.
- Scarcity - about something in short supply, like concert tickets, money or a cure for medical conditions. Fear of missing out on a good deal or opportunity can make you respond quickly.
- Current events - Criminals often exploit current news stories, big events or specific times of year (like tax reporting) to make their scam seem more relevant to you.
If it could be genuine
If you think a message or call might really be from an organisation you have an existing relationship with, like your bank, and you want to be sure:
- Go back to something you can trust. Visit the official website, log in to your account, or phone their advertised phone number. Don't use the links or contact details in the message you have been sent or given over the phone.
- Check to see if the official source has already told you what they will never ask you. For example, your bank may have told you that they will never ask for your password.
Make yourself a harder target
Criminals can use publicly available information about you to make their phishing messages more convincing. This could be gleaned from your social media accounts.
To make life harder for the criminals, you can do the following:
- For your social media applications and other online accounts, review your privacy settings.
- Think about what you post (and who can see it).
- Change your phone number to be unlisted or 'ex directory. Instructions here,
Reporting suspicious messages
The message might be from a company you don’t normally receive communications from, or someone you do not know. You may just have a hunch. If you are suspicious, you should report it. By doing so you'll be helping to protect many more people from being affected.
If you have received an email which you’re not quite sure about, forward it the Suspicious Email Reporting Service (SERS) at report@phishing.gov.uk
Website
If you have come across a website which you think may be fake and trying to scam you, report it using the online form here.
Text message
Phone providers allow you to report suspicious text messages for free using the shortcode 7726.
Forwarding a suspicious text message on an iPhone
- Take a note of the number that sent you the message.
- Enter the conversation then press and hold on the message bubble.
- Tap More.
- Select the message or messages you want to forward.
- Tap the arrow on the bottom right of your screen.
- Input 7726 and send.
Forwarding a suspicious text message on an Android phone
- Take a note of the number that sent you the message.
- Enter the conversation then press and hold on the message bubble.
- Tap on the three vertical dots on the top right of your screen.
- Tap Forward.
- Input 7726 and send.
What to do if you've already responded
If you've already responded to a suspicious message, take the following steps:
- If you’ve been tricked into providing your banking details, contact your bank and let them know.
- If you think your account has already been hacked refer to the guidance on recovering a hacked account here..
- If you received the message on a work laptop or phone, contact your IT department and let them know.
- If you opened a link on your computer, or followed instructions to install software, open your antivirus (AV) software if you have it, and run a full scan and allow your antivirus software to clean up any problems it finds, further guidance here.
- If you've given out your password, you should change the passwords on any of your accounts which use the same password, if you need help, click here.
- If you've lost money, tell your bank and report it as a crime to Action Fraud (for England, Wales and Northern Ireland) or Police Scotland (for Scotland). By doing this, you'll be helping the battle against criminal activity, and in the process prevent others becoming victims of cyber crime.
Training
NCSC has created e-training that guides businesses through the actions they should take in order to reduce the risk of the most common cyber attacks, such as ransomware** and phishing*.
**Ransomware is malware (any type of malicious software designed to harm or exploit any programmable device, service or network) that employs encryption (process of translating plain text data into something that appears to be random and meaningless) to hold a victim's information at ransom. A user or organisation's critical data is encrypted so that they cannot access files, databases, or applications. A ransom is then demanded to provide access.
It has has been designed so that any small organisation, regardless of the level of existing cyber security knowledge, can understand the online threats they face and take steps to improve their cyber defences. Click click here for the training information.
Here are some examples of scam e mails: